TOTP (Google Authenticator)
You can enable Time-Based One-Time Password authentication in the Ory Identity Service (Kratos) to allow users to perform 2FA with TOTP apps such as the Google Authenticator.
When enabled, users can pair a TOTP app with their account:
note
The example screenshot is captured using the Ory Managed UI.
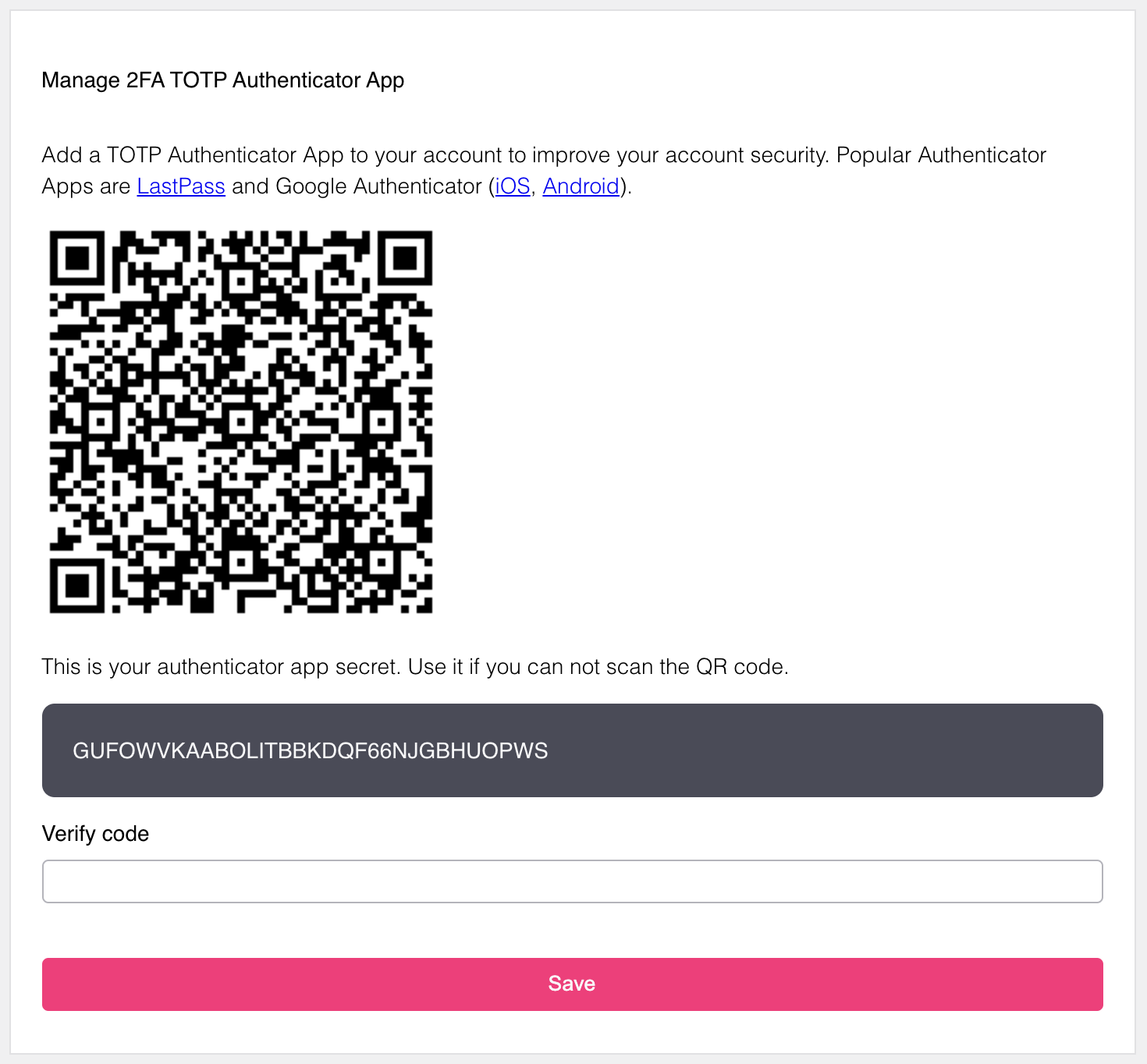
When attempting to perform actions secured with 2FA, users get a TOTP code with the application identifier:
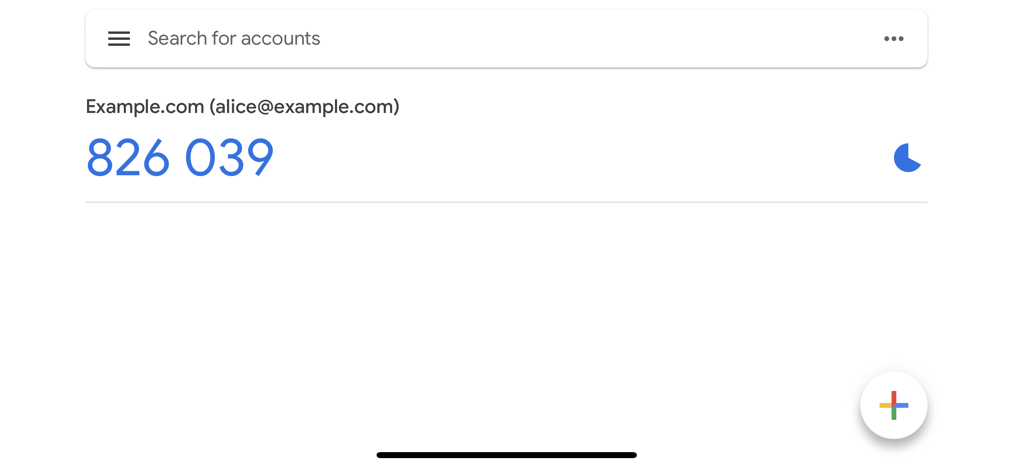
info
In this example, the user identifier (email - alice@example.com) is used. To learn how to enable this behavior, read
this section.
Configuration
Follow these steps to enable Time-Based One-Time Password (TOTP) as the second authentication factor:
Ory Cloud Console
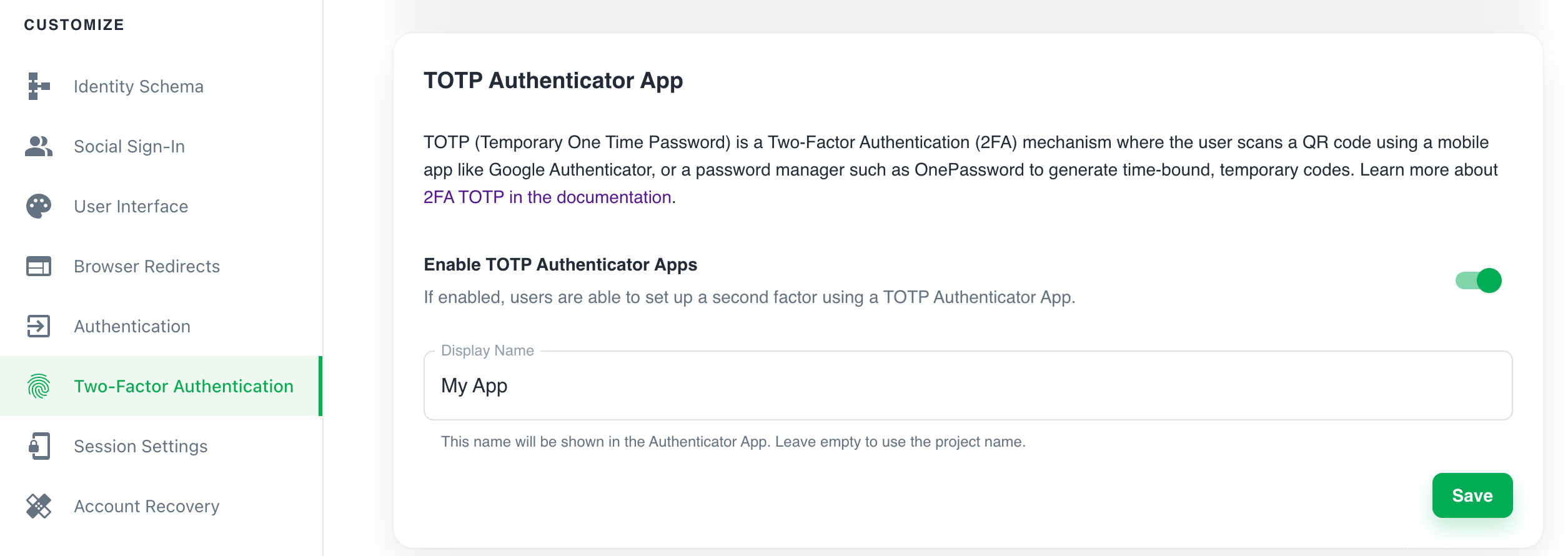
- Sign in to the Ory Cloud Console and go to Two-Factor Authentication.
- In the TOTP Authenticator App section, use the switch to enable TOTP.
- Define the name of the requesting party in the Display Name. The users sees this name in the TOTP application when getting a one-time password.
- Click Save to finish.
Ory CLI
- Get the Identity Service configuration from your project and save it to a file:
## List all available projects
ory list projects
## Get config
ory get identity-config <project-id> --format yaml > identity-config.yaml
- Find
totpinselfservice/methods, setenabledtotrue, and define theissuer:
selfservice:
methods:
totp:
config:
# The "issuer" is the name in the TOTP application users see when getting a one-time password.
issuer: ExampleIssuer.com
enabled: true
- Update the Ory Cloud Identity Service configuration using the file you worked with:
ory update identity-config <project-id> --file identity-config.yaml
Self-Hosted Instances
When working with self-hosted instances of the Ory Identity Service (Kratos), add the totp method to selfservice/methods in
the configuration file:
selfservice:
methods:
totp:
config:
# The "issuer" is the name in the TOTP application users see when getting a one-time password.
issuer: ExampleIssuerForSelfHosted.com
enabled: true
Distinguishing Identities Requesting TOTP
To help users distinguish which identity requests for the TOTP code, add a totp object to the trait which represents the TOTP
account name.
In this example, the user's email address is the identifier:
note
This configuration is the default for all Ory Cloud projects.
{
"$schema": "http://json-schema.org/draft-07/schema#",
"type": "object",
"properties": {
"traits": {
"type": "object",
"properties": {
"email": {
"type": "string",
"format": "email",
"title": "Your E-Mail",
"minLength": 3,
"ory.sh/kratos": {
"credentials": {
// ...
"totp": {
"account_name": true
}
}
// ...
}
}
// ...
}
// ...
}
}
}
Writing E2E Tests
When writing end-to-end (E2E) tests for TOTP implementation in your app, you can reference the Cypress tests used in Ory Identity Service (Kratos).